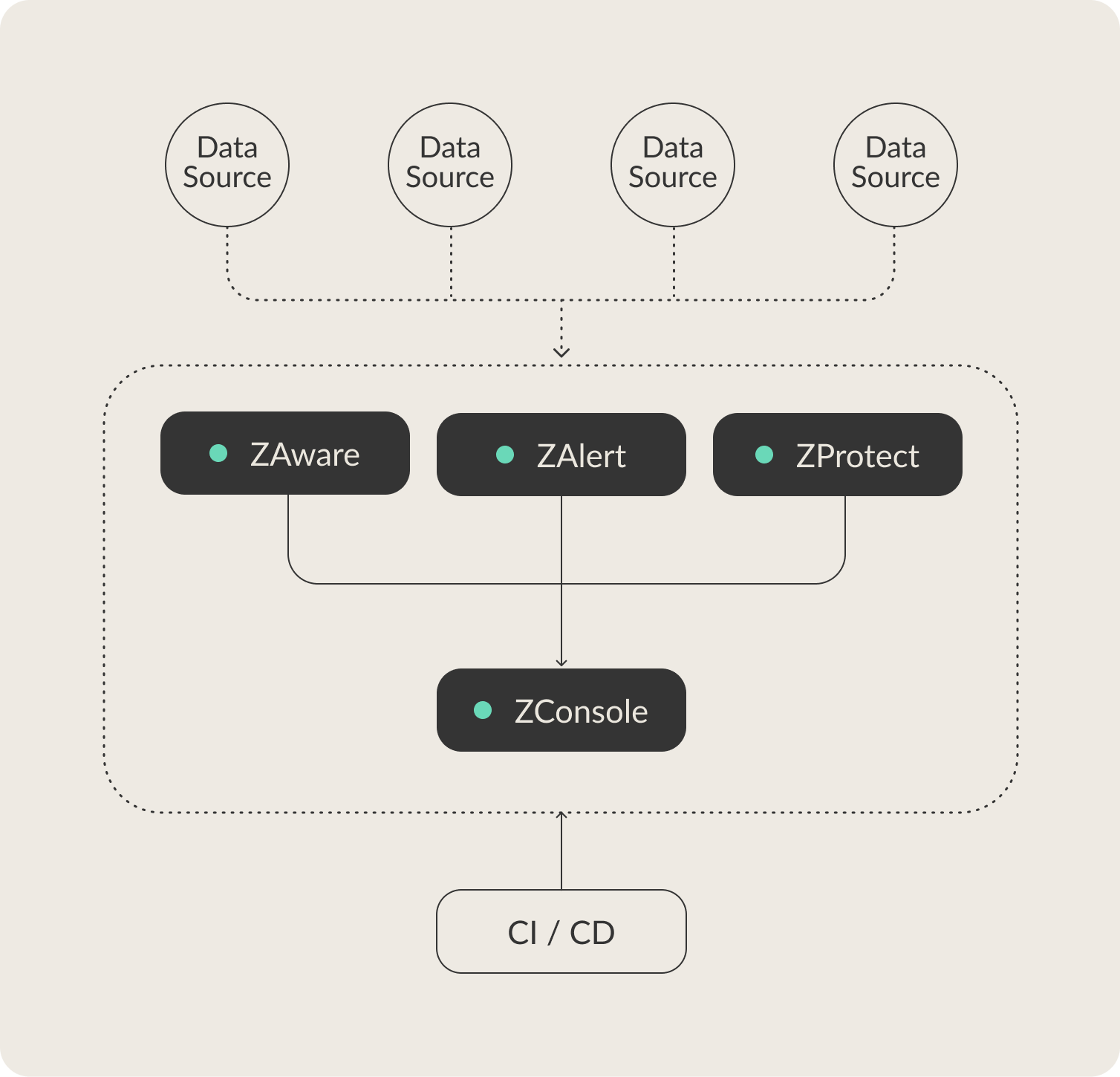
About our solutions
Delivering a practical path to achieve digital visibility.
Who we are
Delivering a practical solutions to achieve digital visibility.
Our technology has being deployed to be user-friendly, affordable cyber security suite of solutions based on Zero Trust principles that facilitate digital visibility and threat response